Petroleum producers have been hearing about the promise of the digital oil field for more than 20 years. Now, just when it looked like it was about to surge, a problem emerged: making the most of digital connectivity requires standards-based technology, which unfortunately can come with cyber vulnerability.
Mainstream operational technology (OT) suppliers hadn’t taken that into account in their technology architectures, leaving wellsite operators wondering how much to invest in adding firewalls and other IT to protect the aged controls into which they were now locked. Many have chosen to forego any benefit that the Industrial Internet of Things, cloud or data analytics may deliver, waiting for a better solution. Finally, the following trends have converged to make the digital oil field feasible:
• The embedding of military-grade authentication and encryption technology deeply into OT;
• The emergence of communication and integration software standards that can use advanced authentication and encryption to secure data exchange among field devices and operations improvement applications; and
• Semiconductor price/performance that continues to advance, roughly as Moore’s law has predicted.
Effective security starts in OT hardware
Mission-critical OT for well sites includes programmable logic controllers, remote terminal units, distributed control systems or other control technology that automate control pumps, gas lifts, valves and all other production elements based on signals from field instruments. Breach of any of these systems can result in millions of dollars a day in lost production, safety risk or theft of intellectual property.
Cybersecurity practices that military, aerospace and online commerce industries use to secure their operations have proven effective, but they have not been available to wellsite operators because the sites were heavily invested in automation technology that was designed before cybersecurity was an issue. Now, however, these cybersecurity solutions—based on public key infrastructures (PKIs)—are finding their way onto the oil field.
In a PKI, a third party known as a certificate authority assigns unique identifying certificates to all participants or devices that require access to data or controls. Once set up, a PKI mediates access to data and devices in real time. Message sources and destinations are authenticated and the content is end-to-end encrypted. Each device in the system becomes responsible for its own security. For example, the information in certificates allows a controller to know that a message changing a set point comes from a known operator with adequate privileges. Security no longer depends on firewalls, intrusion detection devices or other technology that attempts to filter access. These bolted-on perimeter protections can be breached easily by hackers. Cracking properly implemented PKI cryptography, however, is well beyond the ability of most sophisticated hackers (Figure 1). Trust no longer relies on a secure network but on secure end points. Communications can flow securely over otherwise insecure links, including the internet.
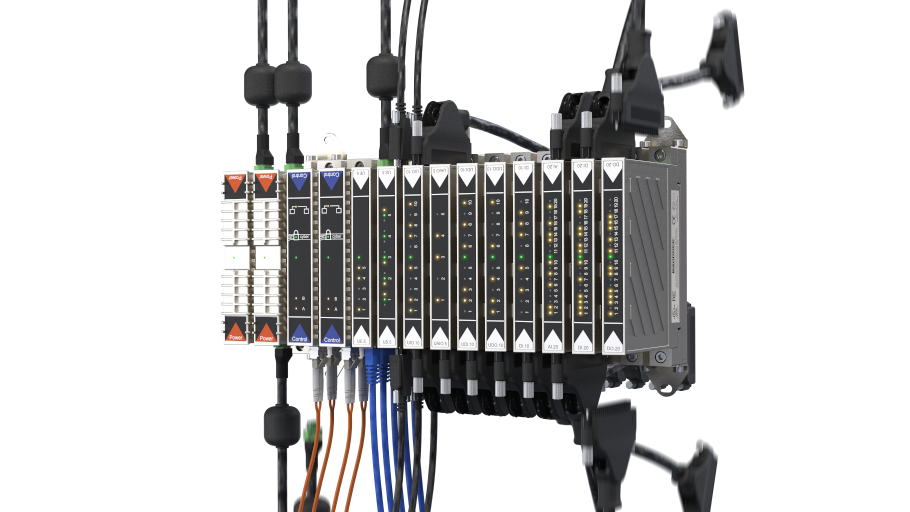
An industrial device with a built-in PKI is essentially immune to cyber penetration, but it must be designed in it from the beginning. Intrinsic security of this depth rests on secret electronic keys that have been burned into the silicon in the manufacturing process. This is critical to ensure that the control processor boots up securely because the first code it encounters cannot be encrypted. Protecting this code with signatures or checksums assigned afterward will not work, because anyone that can access that information can breach the system. Multistage verification based on keys that only the system hardware will ever know provides maximum security. This is why it is also critical to assess the integrity of the component supply chain of any supplier of critical automation technology.
Securing data exchange
Embedding cybersecurity PKI into automation technology eliminates the possibility of unauthorized access to critical controls, and the third-party root of trust it provides can secure open data exchange.
Digital transformation, Big Data analytics and the Internet of Things are all hot topics. The underlying premise is that data can and should be able to flow anywhere needed. For example, there is no need to roll a truck to a wellhead just to check some values and perhaps tweak some adjustments. These things can be done remotely. With today’s technology, a wellhead can report a wealth of production and diagnostic information and even be controlled from the far side of the planet. At the field level, this means fewer and more focused truck rolls. At the enterprise level, it becomes possible to dynamically optimize the operation of the entire oil field using a combination of well data, reservoir models and market conditions.
The enabling technology has two parts. First, for data to flow, computers must understand each other. Just as people communicate using a common language, computers rely on protocols. Some protocols are proprietary and others are based on open standards. Adherence to open industry standards reduces the cost of implementing, operating and maintaining automation systems while optimizing performance.
Secondly, anywhere is not everywhere. The protocols must be not only open but also secure. The gold standard for secure communication is PKIbased mutual authentication and encryption. This ensures that any message looks like gibberish to an eavesdropper and also ensures it flows from the intended source to the intended destination. If properly implemented, the cryptography is for practical purposes unbreakable without access to the secret keys. The ability to protect keys is the foundation of intrinsic security. It must be built in.
OPC UA and MQTT
Both open platform communications unified architecture (OPC UA) and message queuing telemetry transport (MQTT) are open protocols that simplify the integration of open data flows. They also both include provisions for PKI security in their specification. OPC UA is fast becoming an important communication standard for managing open communications across multivendor applications and devices across a network. To access data, an OPC UA client program, for example a SCADA system, connects to OPC UA servers and allows multiple SCADA human machine interfaces or other clients to connect and exchange data.
MQTT is a global standard messaging protocol, which is designed to optimize connections with remote locations with minimal code. It is becoming increasingly valuable for connecting intelligent devices and providing bandwidth efficient cloud connectivity, such as the architecture shown in Figure 2.
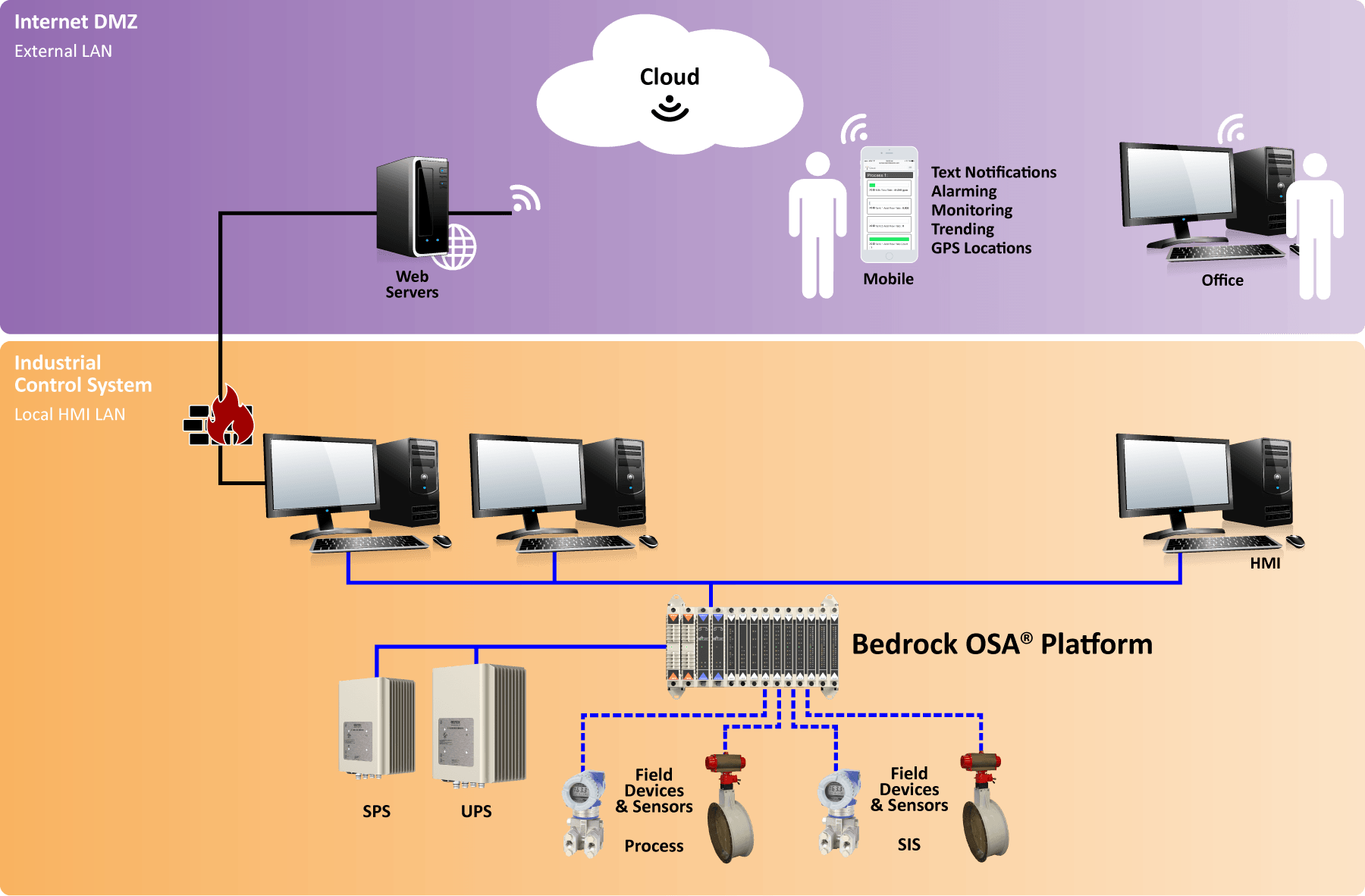
Performance and security at the speed of Moore
The third essential enabler of the digital oil field is the advancement of semiconductor performance, roughly following Moore’s law, which predicts that the number of transistors in densely integrated circuit doubles about every two years.
Maximum bandwidth at affordable prices is critical for at least two reasons. One is that conducting so many real-time authentication and decryption operations in a high output processing environment requires more bandwidth than most systems have today. Second, with security at the control and data exchange level, it is possible to enjoy the advantages of Big Data to achieve the benefit of the digital oil field fully. Real-time production data can help monitor production in real time, manage assets more strategically and manage flow more effectively. As more control capability is pushed out to the field, the need for maximum bandwidth and storage is increasingly essential to being able to tap into the full potential that a secure, digitally enabled oil field can now deliver.
Have a story idea for Tech Watch? This feature highlights leading-edge technology that has the potential to eventually address real life upstream challenges. Submit your story ideas to Group Managing Editor Jo Ann Davy at jdavy@hartenergy.com.
Recommended Reading
Rhino Taps Halliburton for Namibia Well Work
2024-04-24 - Halliburton’s deepwater integrated multi-well construction contract for a block in the Orange Basin starts later this year.
Halliburton’s Low-key M&A Strategy Remains Unchanged
2024-04-23 - Halliburton CEO Jeff Miller says expected organic growth generates more shareholder value than following consolidation trends, such as chief rival SLB’s plans to buy ChampionX.
Deepwater Roundup 2024: Americas
2024-04-23 - The final part of Hart Energy E&P’s Deepwater Roundup focuses on projects coming online in the Americas from 2023 until the end of the decade.
Ohio Utica’s Ascent Resources Credit Rep Rises on Production, Cash Flow
2024-04-23 - Ascent Resources received a positive outlook from Fitch Ratings as the company has grown into Ohio’s No. 1 gas and No. 2 Utica oil producer, according to state data.
E&P Highlights: April 22, 2024
2024-04-22 - Here’s a roundup of the latest E&P headlines, including a standardization MoU and new contract awards.





