
A company's demonstrated ability to manage and mitigate cyber risk can impact everything from insurance rates, to investment levels, to its competitive position in the market. (Source (all images): ABS Group)
Cybersecurity is a challenging concept for any organization. Cyber is often highly technical, too abstract and is constantly changing. Although there is a lot of guidance and opinions, there is no clear checklist of steps to follow. It is also hard to see the threat and to believe that an organization can be a target. As a new expense, and with no clear return on investment, developing a robust cybersecurity program can seem daunting, confusing and impractical.
The reality is that cyber threats for offshore are growing, both in number and severity. A simple explanation of cyber is needed to provide some practical guidance on how to approach it.
Safety Issues and Operational Risks
Cyber threats are getting real.
Cyber attackers are moving beyond stealing corporate data. They are now threatening real-world operations. Cyber attackers have broadened their reach from traditional information technology (IT) systems to targeting operational technology (OT) networks and devices. This means that the threat is moving from onshore enterprise networks to the operations and safety of vessels and facilities.
While traditional cyber attacks are aimed at gaining a financial advantage or disrupting business activities, newer OT attacks are geared at disrupting or stopping real-world operations. For example, GPS spoofing can redirect or disable a drillship navigating to its remote location. Hacking into an offshore facility’s devices, equipment and sensors can also paralyze safety systems, disrupting and taking operations offline. This means that cybersecurity is now a vessel, facility, public and environmental safety issue. Attackers are now disrupting, destroying and delaying daily operations.
If digitalization is a new market reality, then cybersecurity is a business imperative.
Digital transformation opened a world of new opportunities in offshore operations. Data enhancements made assets “smarter”, exploration expanded into more remote, harsher environments and industry began producing more with less, faster, while using data to improve HSE practices. But as connectivity grows and dependency on automation expands, so does cyber risk. Cyber is now, and will continue to be, a part of doing business.
There is Guidance, But No Single Solution
One of the most commonly used guidelines for cyber risk management is the NIST Cyber Security Framework (CSF). NIST CSF compiled international standards into a non-prescriptive set of outcomes that, if achieved, result in a secure cyber system. NIST CSF is designed to work in any business or industry and is effective for offshore facilities. NIST CSF breaks cybersecurity into five functions: identify, protect, detect, respond and recover.
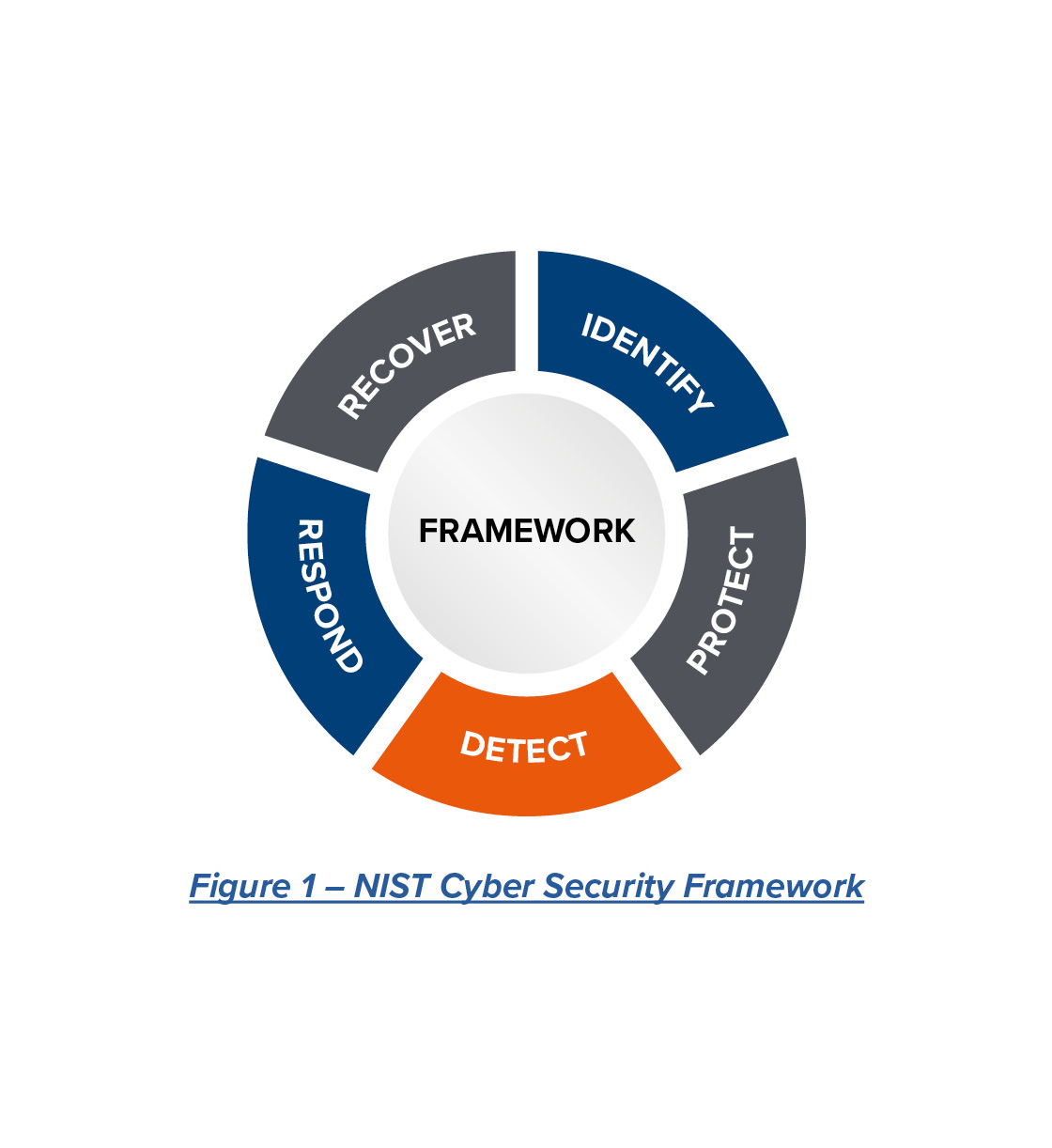
However, frameworks and standards, such as NIST CSF, cannot provide a prescribed set of solutions for cyber risk management. There is no single checklist that applies to all companies. Each organization is unique, and a robust cybersecurity program needs to account for multiple factors, including risk environments, fleet and facility composition, strategic growth plans, connectivity and existing IT and OT cyber capabilities.
Building an individualized IT and OT program can seem daunting. However, any organization can break down the effort into three categories: Assess and Plan; Protect and Defend; and Detect and Respond.
Assess and Plan
Know your risk. Have a plan.
Safety bodies such as the International Maritime Organization (IMO) specify that effective cyber risk management should consider the safety and security impacts resulting from the exposure or exploitation of cyber vulnerabilities in both IT and OT systems.
A good place to begin is with an IT and OT cybersecurity maturity gap assessment. There are a number of maturity assessments available, but they typically include a common set cyber risk controls, such as asset and vulnerability management, vendor management, training, detection and incident response. Consider using third-party organizations that have the cyber IT, OT and offshore expertise to guide you through the process.
In addition to maturity assessments, supportive activities include a cyber asset inventory, security architecture assessment, cyber policy review and a vulnerability scan. By understanding the connectivity, functions and access across all aspects of a network, an organization can obtain a clear picture of what needs to be protected and what virtual holes exist.
Key facility systems to evaluate could include (but not limited to):
- Bridge navigation systems
- Safety management systems
- Machinery management and power control systems
- Access control systems
- Administrative and crew welfare systems
- Communication systems
Protect and Defend
Build defense in depth and breadth.
A key concept in most cyber guidelines is “defense-in-depth and breadth.” Having “defense-in-depth” includes developing multiple layers of protection and detection measures for robust defenses. Organizations should employ multiple controls, at multiple levels of systems and networks, creating robust resistance to cyber-attacks. Examples of these defense strategies include whitelisting, vulnerability and patch management, asset management, vendor risk management, training and security architecture.
Defense in-breadth means the number of systems and devices protected within the highly interconnected IT and OT networks. By taking a systems-of-systems approach, organizations can develop cybersecurity programs that include the full breadth of potential exposures.
Training is a critical, but often overlooked, part of protecting a cyber network. Understanding how humans play a role in cyber risk management is important. Whether from human error, the revolving nature of staffing an offshore facility or a malicious cyber-attack, understanding how your exposure points are expanding and what to do about it will help reduce risk to HSE.
Detect and Respond
Cyber intrusions are not a question of “if” but of “when.”
Organizations that actively monitor and prepare for cyber intrusions take advantage of the visibility and control to efficiently detect, respond and remediate a cyber intrusion. Whether an attack is targeted, or an organization is caught by a broad-based attack, the ability to quickly identify and resolve an intrusion is critical to limiting the impact an attacker can have on a network.
Monitoring capabilities should cover IT and OT networks, both at onshore enterprises and offshore facilities. The more complete the picture, the more effective the monitoring. An effective monitoring system requires domain expertise. Cyber management companies must understand offshore networks, connectivity and environments to effectively protect offshore facilities.
Response programs need to account for the technical, legal and organizational dimensions. Well prepared organizations, prepare, practice and continuously learn from their cyber detection and response programs.
In March 2020, the U.S. Coast Guard (USCG) published Navigation and Inspection Circular (NVIC) 01-20, confirming that the assessment and planning for cyber vulnerabilities is a requirement under the nation’s Maritime Transportation Security Act (MTSA) regulations for Outer Continental Shelf facilities. This NVIC provides guidance to facility owners and operators on complying with the requirements to assess, document and address computer system and network vulnerabilities.
MTSA regulations require that any cybersecurity vulnerabilities identified in the facility security assessment must be addressed in the facility security plan or alternative security program.
Cybersecurity is a rapidly changing risk for everyone. Creating and cultivating adaptive cyber protection, defense and response program goes a long way to minimizing the likelihood of a successful attack and the impact of an intrusion, allowing offshore companies to keep the cyber risk equation in their favor.
_____________________________________________________________________________________
[SIDEBAR]
Mobile Apps to Support Digital Transformation
The number of data-related tasks to safely and efficiently manage offshore facilities is also growing exponentially. In addition to regulatory safety drivers, operators must monitor their performance activities and operations to maintain compliance and competitiveness in an increasingly connected world.
The NS Vessel mobile and desktop applications from ABS Nautical Systems (NS) are designed specifically for vessels operating globally, across the deep waters of open oceans. The applications are simple to deploy and support day-to-day activities onboard blue-water vessels used for offshore operations. Vessel tasks to facilitate maintenance and compliance are simplified and easily viewable, ensuring action can be taken efficiently and rapidly. These applications enable compliance with regulations and help to reduce third-party audit time onboard. They also help staff and crew manage effort and cost and provide better data for decision support.
The NS Vessel mobile app for the OSV sector is cloud-based and accessible using a tablet or smartphone. Because the app is optimized for tablets and smartphones, its interface is simple and intuitive to use, with limited training required. By simplifying tasks and making them easily viewable, the application boosts crew mobility and ensures efficiency as daily tasks, inspections and checklists are performed.
Recommended Reading
Laredo Oil Subsidiary, Erehwon Enter Into Drilling Agreement with Texakoma
2024-03-14 - The agreement with Lustre Oil and Erehwon Oil & Gas would allow Texakoma to participate in the development of 7,375 net acres of mineral rights in Valley County, Montana.
First Solar’s 14 GW of Operational Capacity to Support 30,000 Jobs by 2026
2024-02-26 - First Solar commissioned a study to analyze the economic impact of its vertically integrated solar manufacturing value chain.
SunPower Begins Search for New CEO
2024-02-27 - Former CEO Peter Faricy departed SunPower Corp. on Feb. 26, according to the company.
Green Swan Seeks US Financing for Global Decarbonization Projects
2024-02-21 - Green Swan, an investment platform seeking to provide capital to countries signed on to the Paris Agreement, is courting U.S. investors to fund decarbonization projects in countries including Iran and Venezuela, its executives told Hart Energy.
GE Vernova Completes Spin-Off from GE
2024-04-04 - GE Vernova, an energy transition company, began trading as an independent company on the New York Stock Exchange this week.





